Session Vs Token Authentication
What is session Authentication and token authentication ?. Why session or token authentication as a solution for a web app.....
Table of contents
Contents
- HTTP
- Session Authentication
- Cookies
- Token Authentication
- JWT (JSON web tokens)
- Benefits of Token Authentication
- Benefits of Session Authentication
1) HTTP
Connection made from a client to a server is made using the HTTP protocol and unfortunately the protocol is stateless. This means once the client requests hits the server and the server sends a response, the connection becomes exhausted like a "mission completed" scenario, and hence we tend to say that there is no state between both client and server, that is to say there is no way for the server to remember the client and same for client to server. It's like saying there is an amnesia for both server and client and they kind of become peter parker to the world in spiderman no way home lol.
Relating with Authentication, if a user makes a login request to a server, the server checks if data being sent are correct (i.e validating data to ensure it's the right user accessing the login), then sends a response back to the user (client) telling the client the user exists in the database and its valid, then gives access to that user to access any route as the user is authenticated.
But, for any subsequent requests made by that user even in that same instance, the server prompts the user to login again. why? , Because the Protocol ensuring the connection is stateless and with the example from the first paragraph, the server forgets about the client ever making that particular request.
And this is poor UX, meaning for every request sent to the server the client will always have to login again, which means during the stay in the app or web app, the client might have to login about a 100 times within a hour if i am not exaggerating.
And then came the birth of session Authentication.
2) Session Authentication
Session Authentication makes the protocol a "stateful" one and ensures subsequent requests do not need to always make the user login for every request, but how is it doing that ?
When a user makes a request with some user data, the server checks the data against the database, confirms if it is valid, then send a response with a 200 status back to the client and also sends a Cookie to the client as well. The cookie is what makes it Session Authentication.
Lets use this image below to understand session authentication better before going further and yes credit to "sherry hsu" for the photo on her blog on the same topic sherryhsu.medium.com/session-vs-token-based..
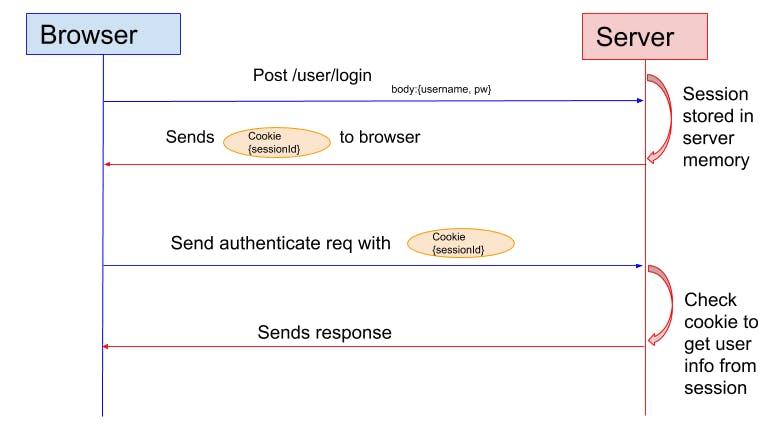
we can see from the above on the blue first line indicating the request with user data being sent from client to server, then the server stores a session on its memory then sends a response to the client with a cookie as well and for every subsequent request, the cookie is sent along helping the server remembering the connection made hence making it "stateful", it's okay if you dont understand this, this was just a summary of everything because of the image....
3) Cookie
What is a cookie ? A cookie is a bit of information stored on the client computer through the browser. It is unique because it gets sent to the server automatically for every request. The cookie being sent to the server in this case contains a "session" created by the server.
A session is just an object or a dictionary in python, that stores user information.
What does the session contain by default?
A session ID and some other information (username, email, e.t.c). The session ID is most important here cause aside your cookie, the whole process of the session authentication revolves around the session ID.
Now we've known the that the server creates a session, stores it in a cookie, and sends the cookie to the browse for subsequent requests. How does the session Authentication then authenticates?
The server doesnt just send the session through a cookie to the browser, it as well stores the session to the server memory as well. This means , it has the session on the server and on the client as well, and when requests are made, the session ID is extracted from the cookie sent automatically to the server and then compared to the session ID on the server memory.
If the IDs are true i.e
cookie_sessionID === sessionID_memory ,
the user is still authenticated till the cookies either get expired or the session ID deleted from it or maybe deleted from the server's memory, till then the connection becomes "stateful" and user is authenticated.
And thats how session Authentication works...
Planning on breaking the Whole post content down to two parts, one for session Authentication and the other for JWT. It will make more sense you understand fully and not just follow my judgement on my summary which will be from my own experience, so take your time , read this , try to understand , and expect the next content tomorrow, for now, Happy coding.
Link to part 2 backendharry.hashnode.dev/session-vs-token-..